QARMA
QARMA (from Qualcomm ARM Authenticator[1]) is a lightweight tweakable block cipher primarily known for its use in the ARMv8 architecture for protection of software as a cryptographic hash for the Pointer Authentication Code.[2] The cipher was proposed by Roberto Avanzi in 2016.[2][3] Two versions of QARMA are defined: QARMA-64 (64-bit block size with a 128-bit encryption key) and QARMA-128 (128-bit block size with a 256-bit key). The design of the QARMA was influenced by PRINCE and MANTIS.[3] The cipher is intended for fully-unrolled hardware implementations with low latency (like memory encryption). Unlike the XTS mode, the address can be directly used as a tweak and does not need to be whitened with the block encryption first.
Architecture
[edit]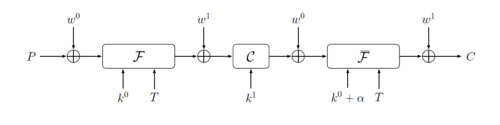
QARMA is an Even–Mansour cipher using three stages, with whitening keys w0 and w1 XORed in between:
- permutation F is using core key k0 and parameterized by a tweak T. It has r rounds inside (r = 7 for QARMA-64, r = 11 for QARMA-128);
- "central" permutation C is using key k1 and is designed to be reversible via a simple key transformation (contains two central rounds);
- the third permutation is an inverse of the first (r more rounds).
All keys are derived from the master encryption key K using specialisation:
- K is partitioned into halves as w0 Concatenation k0, each will have halfsize bits;
- for encryption w1 = (w0 >>> 1) + (w0 >> (halfsize-1));
- for encryption k1 = k0;
- for decryption, the same design can be used as long as k0+α is used as a core key, k1 = Q•k0, w1 and w0 are swapped. α here is a special constant and Q a special involutary matrix. This construct is similar to the alpha reflection in PRINCE.
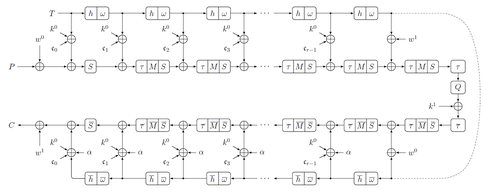
The data is split into 16 cells (4-bit nibbles for QARMA-64, 8-bit bytes for QARMA-128). Internal state also contains 16 cells, arranged in a 4x4 matrix, and is initialized by plaintext (XORed with w0). In each round of , the state is transformed via operations :
- is ShuffleCells, a MIDORI permutation of cells ([ 0, 11, 6, 13, 10, 1, 12, 7, 5, 14, 3, 8, 15, 4, 9, 2]);
- is MixColumns: each column is multiplied by a fixed matrix M;
- is SubCells: each cell is transformed using an S-box.
The tweak for each round is updated using :
- is a cell permutation from MANTIS ([ 6, 5, 14, 15, 0, 1, 2, 3, 7, 12, 13, 4, 8, 9, 10, 11]);
- is an LFSR applied to each of the cells with numbers [0, 1, 3, 4, 8, 11, 13]. For QARMA-64, the LFSR is (b3, b2, b1, b0) ⇒ (b0 + b1, b3, b2, b1), for QARMA-128, (b7, b6, ..., b0) ⇒ (b0 + b2, b7, b6, ..., b1),
The rounds of consist of inverse operations . Central rounds, in addition to two rounds ( and ), include multiplication of the state by an involutary matrix Q.
References
[edit]Sources
[edit]- Avanzi, Roberto (2016). The QARMA Block Cipher Family (PDF). IACR Transactions on Symmetric Cryptology (ToSC). Vol. 17 (published 8 March 2017). pp. 4–44. doi:10.13154/tosc.v2017.i1.4-44. Archived from the original (PDF) on May 13, 2020.
- Zong, Rui; Dong, Xiaoyang (2016). "Meet-in-the-Middle Attack on QARMA Block Cipher" (PDF). iacr.org. IACR. Retrieved 10 June 2022.
- Kaur, Jasmin; Kermani, Mehran Mozaffari; Azarderakhsh, Reza (1 January 2022). "Hardware Constructions for Lightweight Cryptographic Block Cipher QARMA With Error Detection Mechanisms". IEEE Transactions on Emerging Topics in Computing. 10 (1): 514–519. doi:10.1109/TETC.2020.3027789. eISSN 2376-4562. S2CID 226665710.
- Li, Rongjia; Jin, Chenhui (4 May 2018). "Meet-in-the-Middle Attacks on Reduced-Round QARMA-64/128". The Computer Journal. 61 (8): 1158–1165. doi:10.1093/comjnl/bxy045. eISSN 1460-2067. ISSN 0010-4620.
- Yang, Dong; Qi, Wen-feng; Chen, Hua-jin (2018). "Impossible Differential Attack on QARMA Family of Block Ciphers". Cryptology ePrint Archive.












