Carna botnet
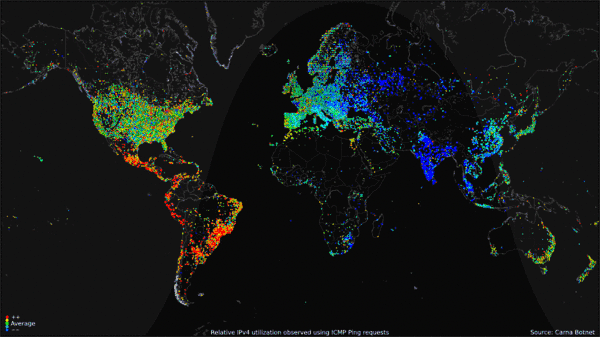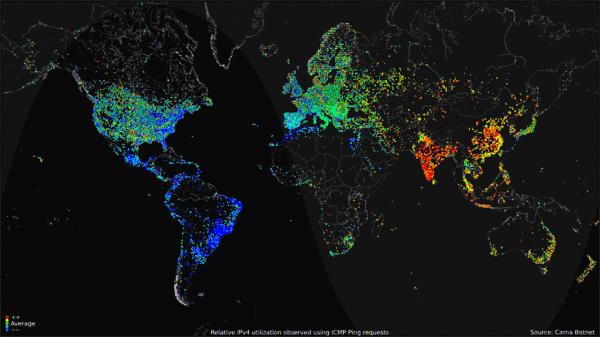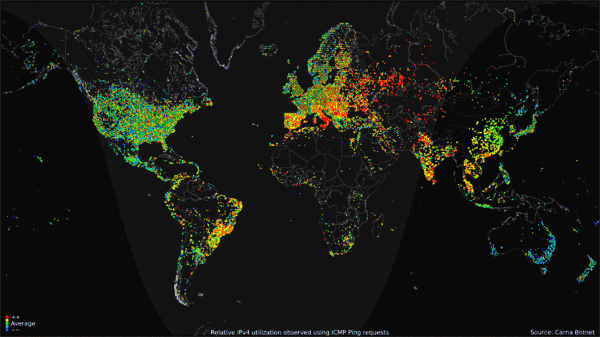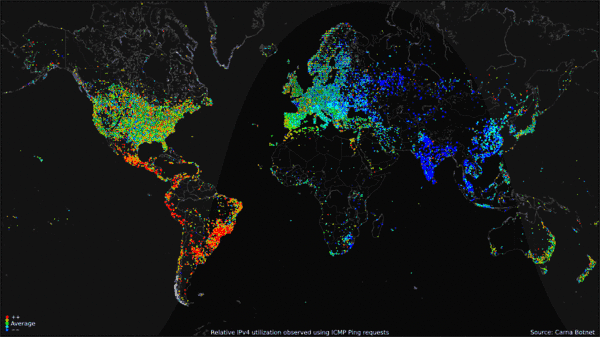
The Carna botnet was a botnet of 420,000 devices created by an anonymous hacker to measure the extent of the Internet in what the creator called the “Internet Census of 2012”.
Data collection
[edit]The data was collected by infiltrating Internet devices, especially routers, that used a default password or no password at all.[1][2] It was named after Carna, "the Roman goddess for the protection of inner organs and health".[3]
Collected data was compiled into a GIF portrait to display Internet use around the world over the course of 24 hours. The data gathered included only the IPv4 address space and not the IPv6 address space.[4][5]
The Carna Botnet creator believes that with a growing number of IPv6 hosts on the Internet, 2012 may have been the last time a census like this was possible.[3]
Results
[edit]Of the 4.3 billion possible IPv4 addresses, Carna Botnet found a total of 1.3 billion addresses in use, including 141 million that were behind a firewall and 729 million that returned reverse domain name system records. The remaining 2.3 billion IPv4 addresses are probably not used.[6]
An earlier first Internet census by the USDHS LANDER-study had counted 187 million visible Internet hosts in 2006.[7][8]
Further implications
[edit]The data provided by the Carna botnet was used by security researcher Morgan Marquis-Boire to determine in how many countries FinFisher spyware was being used. The use of such legally-gray data to conduct open source analysis raised questions for some, but Marquis-Boire expressed a belief that data is data. "I consider this more like rogue academia rather than criminal activity," he told Wired Magazine.[9]
Number of hosts by top level domain
[edit]Amongst other, Carna Botnet counted the number of hosts with reverse DNS names observed from May to October 2012. The top 20 Top Level Domains were:
| Number of hosts[10] | Top Level Domain |
|---|---|
| 374,670,873 | .net |
| 199,029,228 | .com |
| 75,612,578 | .jp |
| 28,059,515 | .it |
| 28,026,059 | .br |
| 21,415,524 | .de |
| 20,552,228 | .cn |
| 17,450,093 | .fr |
| 17,363,363 | .au |
| 17,296,801 | .ru |
| 16,910,153 | .mx |
| 14,416,783 | .pl |
| 14,409,280 | .nl |
| 13,702,339 | .edu |
| 11,915,681 | .ar |
| 9,157,824 | .ca |
| 8,937,159 | .uk |
| 7,452,888 | .se |
| 7,243,480 | .tr |
| 6,878,625 | .in |
See also
[edit]References
[edit]- ^ Stöcker, Christian; Horchert, Judith (2013-03-22). "Mapping the Internet: A Hacker's Secret Internet Census". Spiegel Online.
- ^ Kleinman, Alexis (2013-03-22). "The Most Detailed, GIF-Based Map Of The Internet Was Made By Hacking 420,000 Computers". Huffington Post.
- ^ a b Internet Census 2012: Port scanning /0 using insecure embedded devices Archived 2015-10-13 at the Wayback Machine, Carna Botnet, June - Oktober 2012
- ^ Read, Max (2013-03-21). "This Illegally Made, Incredibly Mesmerizing Animated GIF Is What the Internet Looks Like". Gawker. Archived from the original on 2013-03-24.
- ^ Thomson, Iain (2013-03-19). "Researcher sets up illegal 420,000 node botnet for IPv4 internet map". The Register.
- ^ Guerilla researcher created epic botnet to scan billions of IP addresses With 9TB of data, survey is one of the most exhaustive — and illicit — ever done. by Dan Goodin, arstechnica, Mar 20, 2013
- ^ Exploring Visible Internet Hosts through Census and Survey ("LANDER" study) by John Heidemann, Yuri Pradkin, Ramesh Govindan, Christos Papadopoulos, Joseph Bannister. USC/ISI Technical Report ISI-TR-2007-640. see also http://www.isi.edu/ant/address/ and video
- ^ Forschung mit illegalem Botnetz: Die Vermessung des Internets Christian Stöcker, Judith Horchert, Der Spiegel, 21.03.2013
- ^ McMillan, Robert (2013-05-15). "Is It Wrong to Use Data From the World's First 'Nice' Botnet?". Wired. Archived from the original on 2016-12-22.
- ^ "Top Level Domains. Internet Census 2012". Archived from the original on 2013-05-15. Retrieved 2013-05-16.
External links
[edit]- Internet Census 2012: Port scanning /0 using insecure embedded devices, Carna Botnet, June — October 2012
- All of the data can be found on GitHub, BitBucket, SourceForge, and Internet Archive.
